Time to read:
In this post we are going to go over how to install Nginx and configure it as a Reverse Proxy for a web page that I am hosting on a local web server.
In my example I am currently hosting my Flame dashboard on a web server in my homelab. I want to configure Nginx on my web proxy server to proxy clients connection to this server using TLS (Transport Layer Security) with certificates issues by my enterprise CA (Certificate Authority).
- SECTION I – What is a Reverse Proxy?
- SECTION II – Intended Setup
- SECTION III – Installation & Configuration
- SECTION IV – Footnotes
SECTION I – What is a Reverse Proxy?
Lets start with explaining what a reverse proxy is by explaining what a proxy server is.
A proxy server sits between clients and the internet. When the a user wants to browse to a web page the client sends a HTTP (Hyper-Text Transport Protocol) request to the proxy server. Then the proxy server will send a HTTP request to the destination that the client initially requested. The proxy will then serve the HTTP reply (the request resource) from the destination to the client. The proxy server sits as an intermediary in the connection.
What is the point of a proxy server? There are a few reasons why a proxy server can be beneficial for a network of clients. One reason is that the proxy server can cache resources that are often accessed by clients, meaning that the outgoing traffic to the internet is reduced and the time the client has to wait to load commonly requested resources is reduced. Another use is that having single exit point for web requests means this is an ideal location to implement an ACL (Access Control List). This means we can dictate that destination domains the clients can load web requests from.
So now we know what a proxy is, lets talk about a reverse proxy. Think about the proxy process but in reverse. A reverse proxy sits between clients that could be within the private network or on the public internet and a web server hosted within the local network. The result is that when clients request resources that are physically located on the local web server they connect to the reverse proxy server in order to access those resources. This obscures the web server or any other local resource from being accessed directly. Additionally, this means that the user doesn’t really know what local resource they are connecting to meaning we can change infrastructure by scaling up or down or changing how the proxy communicates with the web server without the user having to know how to access the moved or changed resource.
Figure 1 is a simple illustration to visualise the differences between proxy and reverse proxy.

FIGURE 1 – Proxy VS Reverse Proxy
SECTION II – Intended Setup
Lets talk about the aim of the configuration that I am about to go through in Section III.
I am hosting a simple static dashboard that is the homepage for my homelab. Currently it is being hosted on my web server using HTTP port 5005.
I am going to configure the Nginx reverse proxy to proxy the client connection to this web server. The reverse proxy will be open on both port 80 and port 443. If a client connects to the reverse proxy using port 80 they will be redirected to port 443 (HTTPS). When the client connects with HTTPS (HTTP Secure) the reverse proxy will be configured to use an enterprise TLS certificate issued by my CA.
Finally, I am going to configure a CNAME record in my DNS (Domain Name System) server to point a common alias to the Nginx reverse proxy.

FIGURE 2 – NGINX Reverse Proxy Setup
SECTION III – Installation & Configuration
Okay lets get to the good bit and actually set this up.
SECTION III – A – Install Nginx
First we need to install Nginx and get it going.
- Download and install Nginx using the following command:
- Start the Nginx service using the following command:
- Set the Nginx service to start on boot using the following command:
- Create the following directories using the following commands:
- certs – for our TLS certificate and key files
- sites-available – for our Nginx configurations
- sites-enabled – for the Nginx configurations we want active
dnf install nginx -y
systemctl start nginx
systemctl enable nginx
mkdir /etc/nginx/certs
mkdir /etc/nginx/sites-available
mkdir /etc/nginx/sites-enabled
SECTION III – B – Main Nginx Configuration File
Now we have Nginx going, lets edit the main configuration file from its default state. By default Nginx is set to listen on port 80 in its main config file.
Open up the Nginx configuration file:
vi /etc/nginx/nginx.conf
Use the ‘#’ to comment out all of the default port 80 server configuration from the ‘server {‘ to the corresponding ‘}’.
Now add the following line under the ‘Include /etc/nginx/conf.d/*.conf;’ line:
include /etc/nginx/sites-enabled/*.conf;
Now your configuration file should look similar to mine in Figure 3.
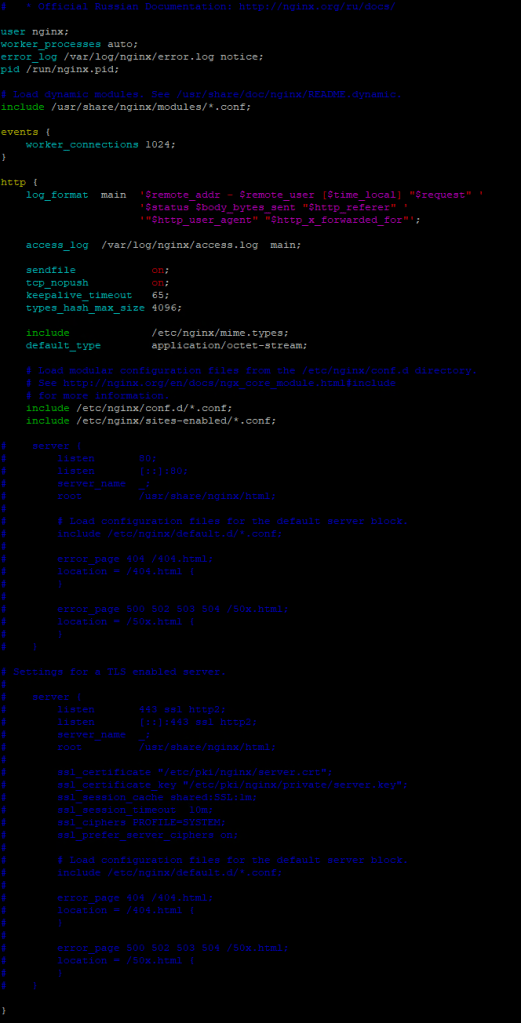
FIGURE 3 – NGINX Main Config File
SECTION III – C – Generate TLS Certificate
Now we need to generate the private key and PKI (Public Key Infrastructure) certificate for our reverse proxy server.
- Make sure you are in your home directory:
- Create a new request file:
- Make your request file looks similar to the example in Example 1: NOTE: if your reverse proxy is going to serve up multiple hostnames then you can put a wildcard DNS name entry in the request file ‘*.example.domain’:
- Enter the following command to generate a CSR (Certificate Signing Request) and private key file:
- Use the cat command to copy the contents of your CSR file:
- The following steps are only applicable if you are using a Windows CA (the goal here is to get a signed certificate from your CA that is in a base64 .crt format):
- Navigate to your CA certserv page:
- Click the ‘Request a certificate’ link.
- Click ‘advanced certificate request’.
- Paste in the contents of your CSR file and select ‘Web Server’ from the certificate template drop down then click submit.
- Select the ‘Base 64 encoded’ radio button and click ‘Download certificate chain’.
- Open the ‘.p7b’ certificate file downloaded in notepad and copy its contents.
- Back on the Nginx proxy server create a new file for the downloaded certificate:
- Run the following command to convert the ‘.p7b’ into a ‘.crt’ certificate file:

Figure 4 – Certserv

Figure 5 – Request a Certificate

Figure 6 – Advanced Request

Figure 7 – Certificate Download
vi filename.p7b
- Now that you have a ‘.crt’ certificate and a private key copy them into the Nginx TLS certificate directory:
cd ~
vi req.conf
[req]
default_bits = 2048
distinguished_name = <FQDN>
req_extensions = v3_req
prompt = no
[<FQDN>]
C = GB
ST = Hilsamlabs
L = Hilsamlabs
O = Hilsamlabs
CN = <FQDN>
[v3_req]
subjectAltName = @alt_names
[alt_names]
DNS.1 = <FQDN>
DNS.2 = <Domain Name>
IP.1 = <IP>
Example 1 – Request Template
openssl req -out filename.csr -newkey rsa:2048 -nodes -keyout filename.key -config req.conf
cat filename.csr
openssl pkcs7 -in filename.p7b –print_certs -out filename.crt
cp filename.{crt,key} /etc/nginx/certs
SECTION III – D – Specific Site Configuration File
Now we can create the configuration file to tell Nginx to be a reverse proxy.
Lets start by creating a new file in our sites-available directory. You can name the file what you want just make sure that it is a ‘.conf’ file:
vi /etc/nginx/sites-available/home.conf
Example 2 is my configuration for the reverse proxy.
server {
listen 80;
server_name noc01webproxy01.hilsamlabs.uk;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl;
ssl_certificate /etc/nginx/certs/noc01webproxy01.crt;
ssl_certificate_key /etc/nginx/certs/noc01webproxy01.key;
location / {
proxy_pass http://noc01websvr01.hilsamlabs.uk:5005;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}Example 2 – NGINX Reverse Proxy Configuration
Lets break down what we are looking at into sections:
- HTTP to HTTPS redirect:
- This portion of the configuration is telling Nginx to listen on port 80.
- Then we have our server name as a variable.
- Then we have the redirect request.
- TLS server listen:
- This portion of the configuration is telling Nginx to listen on port 443.
- Then we set the certificate file and private key file for the HTTPS request.
- Proxy configuration:
- under the TLS server we tell Nginx to do a proxy pass and then the destination of the web request.
server {
listen 80;
server_name noc01webproxy01.hilsamlabs.uk;
return 301 https://$server_name$request_uri;
}Example 3 – NGINX HTTP to HTTPS Redirect
server {
listen 443 ssl;
ssl_certificate /etc/nginx/certs/noc01webproxy01.crt;
ssl_certificate_key /etc/nginx/certs/noc01webproxy01.key;
}Example 4 – NGINX TLS Certificate Configuration
location / {
proxy_pass http://noc01websvr01.hilsamlabs.uk:5005;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}Example 5 – NGINX Proxy Pass
Now we need to get our config file into the ‘sites-enabled’ directory so that Nginx applied the config. To do this we are going to create a symbolic link for the file:
ln -s /etc/nginx/sites-available/filename.conf /etc/nginx/sites-enabled/filename.conf
SECTION III – E – Enable HTTP Routing
Something that may catch you out is SELinux (Security Enhanced Linux)1. We need to specifically set the SELinux policy so that Nginx is allow to route HTTP requests. If we don’t we will get a ‘502 Bad Gateway’ error when you browse to the Nginx reverse proxy.
We can enable this policy by using the following command:
sudo setsebool httpd_can_network_connect 1 -P
SECTION III – F – Open Firewall
The final part of the configuration is to set the host firewall on the Linux device to allow both port 80 and 443 connections.
Do the following 3 commands to allow these ports through the firewall: NOTE: I have included ‘zone internal’ because my interface is in that firewall zone, if yours is not then do not add this part of the command:
firewall-cmd –zone=internal –add-service=http –permanent
firewall-cmd –zone=internal –add-service=https –permanent
firewall-cmd –reload
SECTION III – G – Restart Nginx
Now that everything is configured and good to go we have to restart the Nginx service because we have changed the Nginx configuration files.
To restart the service do the following command:
systemctl restart nginx
SECTION III – H – CNAME Entry
Final part of this project is to add the CNAME entry into our DNS server. In my case I am using a Windows DC (domain controller) so my DNS server is on my DC.
To add the CNAME entry carry out the following:
- Log onto the DC.
- Open up the DNS application.
- In your domains forward lookup zone right click and select ‘New CNAME’.
- Fill out the alias name (home in my case) and then fill out where the alias should point to (my Nginx proxy).

Figure 8 – CNAME Record
SECTION IV – Footnotes
- SELinux – it is a security architecture for the Linux operating system that allows administrators to have more control over who can access the system and its services. It works by defining access controls for applications, processes and files on the system. ↩︎

Leave a comment