Introduction
In this post, we are going to go through how you can easily repair the trust relationship between a Windows Server and its Primary Domain Controller without needing to leave and rejoin the domain.
Section I – The Error
If you have spent much time administrating a Windows domain environment you have most likely come across a very annoying error `The trust relationship between this workstation and the primary domain failed.`
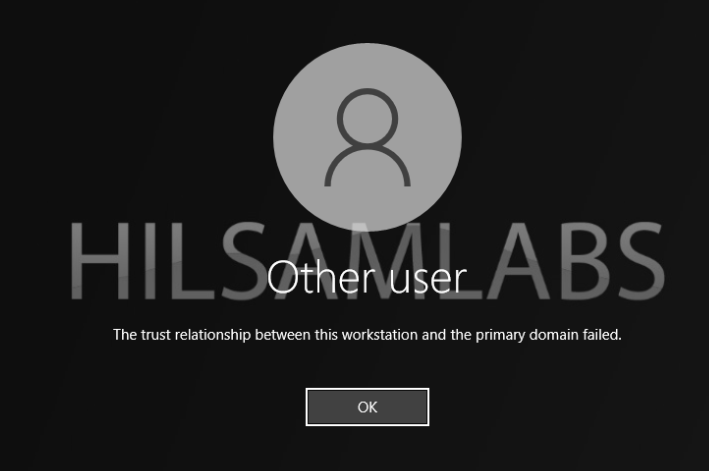
Essentially this error means that the Domain Controller (DC) won’t talk to the computer via a secure communication channel because either the device or the DC has the wrong computer password for the device.
Now I have always gone for the sledge hammer approach of kick the computer off the domain and then rejoin it to the domain. While this works and can be very effective for workstations, it can get a bit stickier when messing around with Windows Servers. What are you supposed to do when you can’t just kick it off? In my case, my homelab’s Certificate Authority (CA) had lost its trust relationship. I for sure was not going down that rabbit hole of kicking him off the domain!
Section II – The Solution
Login to the computer with the broken trust relationship as the local administrator account.
For the username use the following to use the local login:
.\<USERNAME>
Open an elevated PowerShell session by right clicking on PowerShell and selecting ‘Run as Administrator’.
Run the following command:
Test-ComputerSecureChannel -Verbose
If the output is ‘False’ it means that it doesn’t have a connection to the DC.

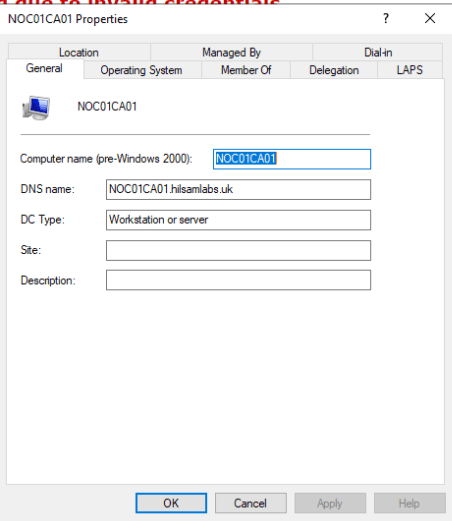
Login to the DC and make sure that the Active Directory (AD) object exists and isn’t locked.
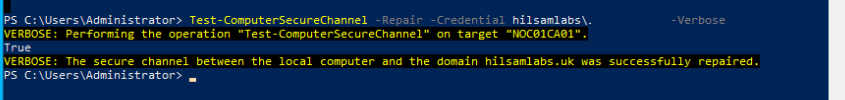
Back on the computer with the broken trust relationship in your elevated PowerShell session run the following command:
Test-ComputerSecureChannel -Repair -Credential <DOMAIN>\<Administrative User> -Verbose
If you see the output from the command as ‘True’ then you know the command has successfully restored the secure channel between the computer and the DC.
Double check the secure channel is working by running the following command again:
Test-ComputerSecureChannel -Verbose
This time you should see a ‘True’ output returned from the command.

Finally, run the following command:
Reset-ComputerMachinePassword -Credential <DOMAIN>\<Administrative User>

Now you should have a full functional trust relationship to your DC from your computer.


Leave a comment