Introduction
In this post, we are going to go over how to get around an error I came across when trying to use Secure Shell (SSH) to access my Cisco C3560CX switch from my Fedora Workstation computer.
Section I – What is SSH?
Secure Shell is a way to control the shell of a remote device with the data transmission secured using authentication and encryption. This allows the SSH session data to be sent over an untrusted network without risk of eavesdropping. This is unlike Telnet which provides the same function but all data is sent in plaintext.
In most modern networks you will use SSH to access the shell of your network devices. Which means you don’t have to get a console cable and physically connect directly to the device you want to manage.
Section II – The Problem
I went through and carried out all of the normal steps to configure SSH on my switch:
username <Username> privilege 15 secret <password> ip ssh version 2 domain name <domain name> hostname <hostname> line vty 0 15 login local transport input ssh transport output ssh crypto key generate rsa modulus 2048
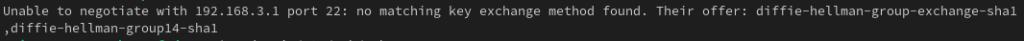
I use Fedora Workstation as my main computer Operating System (OS), so from that device I tried to SSH onto the switch, but, got the following error:
Unable to negotiate with <switch> port <SSH port>: no matching key exchange method found.
Section III – The Solution
This issue comes from the Cisco switch using an older SSH version that only offers older cryptography methods when compared to the later version of SSH that is on my computer. In order to get around this you need to specifically tell SSH on the device you are trying to connect from to allow the key exchange algorithms that the Cisco switch wants to use. There are 2 ways you could do this;
change the global configuration file for SSH
logseq.order-list-type:: number
create a specific configuration file for that device
logseq.order-list-type:: number
I opted to go for the route of a specific configuration file to ensure SSH still stays as secure and robust as possible for all other uses.
Create or edit the following file in your home directory:
vi ~/.ssh/config
add the following making sure it accurately reflects your setup:
Host <Switch IP> User <Username> port <SSH port> KexAlgorithms +diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 Ciphers +aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc PubkeyAcceptedAlgorithms +ssh-rsa HostkeyAlgorithms +ssh-rsa
Now you can SSH onto your switch without any errors, you can accept the newly discovered RSA public key from the switch and then use SSH to remotely administer the switch. NOTE: for the keen eyed, the switch IP address has changed while making this guide but, it is the same switch.


Leave a comment