In this post we are going to be going over the simple fix to the error below. You may encounter this error when you try to change your SSH port on your Linux device from the default of TCP 22 to a different TCP port.
If you would like to see how to correctly change the SSH port on Linux click the link below.
Linux – Change SSH Port on Fedora
SECTION I – The Error
When you try to start or restart the sshd service you will most likely see an output like the one below. Saying something like
Job for sshd.service failed because control process exited with error code.

If we do as the error message suggests and run the following command then we can delve a little deeper into what is going on:
jounralctl -xeu sshd.service
From the above image we can see what the actual error that caused the sshd.service to fail to start was cause by the service being unable to bind the new SSH port that we have configured for SSH to the service.
error: Bind to port (SSH Port) on 0.0.0.0 failed: Permission denied.
SECTION II – The Solution
The error in question is being caused by SELinux. This is because the SSH policy for SELinux isn’t expecting SSH to start on a non-standard SSH port so it is blocking the sshd service from binding that port to that service. SELinux is expecting SSH to bind port 22. We can prove this using the following command:
semanage port -l | grep ssh_port_t
As you can see in the above example the output shows that the SSH policy is expecting TCP port 22.
To allow the newly configured SSH port to be bound to the sshd service we can use the following command:
semanage port -a -t ssh_port_t -p tcp 5379NOTE: in my scenario I have configured SSH to use port 5379 instead of port 22.
Now if we run the same command as earlier we will be able to see that SELinux expects SSH to bind TCP port 5379.
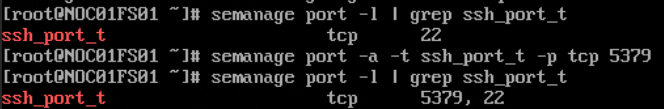
NOTE: SELinux is also still expecting port 22 to be bound to SSH even though the actual SSH service won’t bind to that port anymore. If you want to remove port 22 from this SELinux policy you will have to make your own custom SELinux policy. In my case I don’t have an issue with this because my host firewall is set to block port 22 and the actual sshd service isn’t listening for port 22.
SECTION II – Verification
Now if we run the following command to restart the sshd service:
systemctl restart sshdWe no longer get an error code that causes the service to exit. And then if we check the status of the sshd service we can see that it is running and it is listening on the non-default port we have configured:
systemctl status sshd

Leave a reply to Yaz Cancel reply